Understanding Social Engineering Threats
Social engineering remains one of the most pervasive and insidious threats in cybersecurity. Unlike technical attacks, social engineering exploits human psychology to manipulate individuals into divulging confidential information or performing actions that compromise security. At Radia Perlman Technologies, we’re committed to helping you understand and defend against these sophisticated tactics.
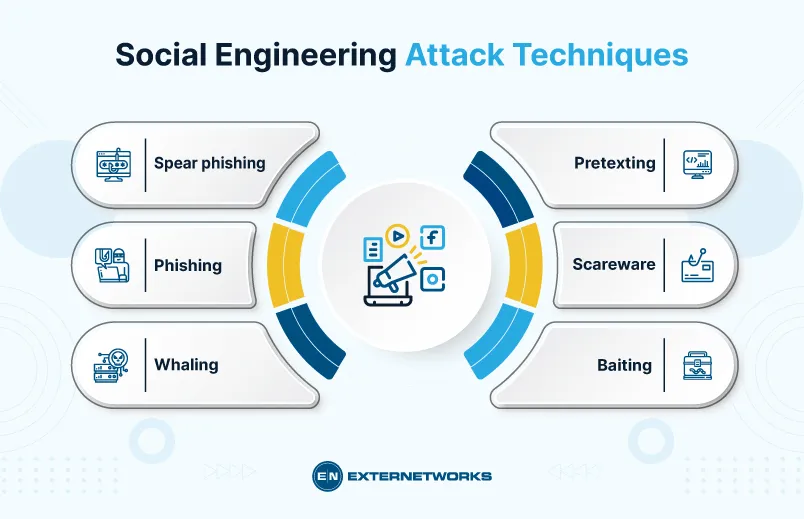
Social engineering attacks can take many forms, including phishing emails, pretexting, baiting, and tailgating. Attackers use various strategies to deceive individuals into revealing sensitive data or granting unauthorized access. Understanding these tactics is crucial for developing effective defense mechanisms.
Key types of social engineering attacks include:
- Phishing: Fraudulent emails or messages designed to trick recipients into revealing personal information or clicking malicious links.
- Pretexting: Creating a fabricated scenario to obtain sensitive information from individuals, often by pretending to be someone they trust.
- Baiting: Offering something enticing to lure individuals into a trap, such as a free download or prize that installs malware.
- Tailgating: Gaining physical access to restricted areas by following authorized personnel, exploiting their trust or politeness.
To mitigate social engineering risks, it's essential to:
- Educate Employees: Regular training on recognizing and responding to social engineering attempts.
- Implement Security Policies: Establish procedures for verifying identities and handling sensitive information.
- Use Multi-Factor Authentication: Enhance security by requiring multiple forms of verification before granting access.
- Monitor and Report: Continuously monitor systems for suspicious activities and encourage reporting of potential threats.
At Radia Perlman Technologies, our cybersecurity experts are here to guide you through the complexities of social engineering threats and develop robust strategies to protect your organization. By fostering awareness and implementing strong security practices, you can significantly reduce your vulnerability to these deceptive attacks.
Learn more about our cybersecurity solutionsFor expert advice and comprehensive protection against social engineering threats, contact Radia Perlman Technologies today.
Reach out to Jane Doe at Radia Perlman Technologies for insights into safeguarding your business from social engineering attacks.
Top Comments

Insightful Read!
August 1, 2024 at 9:33 am
This article provides a clear and comprehensive overview of social engineering threats. The tips for mitigation are practical and essential for any organization looking to enhance its security posture.
Reply
Great Advice!
August 1, 2024 at 10:15 am
The information on social engineering attacks is very helpful. The section on practical steps to combat these threats is particularly valuable for improving our company’s defenses.
Reply
